OT/ICS Security from Armis
Agentless device security for manufacturing and industrial environments.
Agentless
Armis is agentless. No software to install on any device - managed, unmanaged, OT or IoT.
Passive
Completely passive and non-disruptive. Won’t tip over mission critical devices.
Comprehensive
Identifies and classifies all devices in your environment - on or off the network.
Frictionless
No agents. No impact to your network. Can be up and running in as little as minutes.
Agentless and passive OT security that identifies and classifies every connected device, tracks behavior, identifies threats, and takes action to protect safety and operations.
Secure OT, IT, and More
The need for OT security is changing as these environments are rapidly being connected to enterprise networks and exposed to threats coming from the Internet. While these connections make it easy to gather data and remotely manage the OT environment, they also create entry points for attackers. On July 23, 2020, the NSA and CISA issued a joint warning that attackers were actively leveraging these connections to attack OT devices.
Armis is an agentless device security platform that secures all types of connected devices—OT, IT and IoT devices. This is important because attackers see all these connected devices as one continuous system. A siloed security system that myopically sees just one of these environments simply does not keep OT systems secure.
Identify & Prioritize Vulnerabilities
An ICS Security Risk Assessment can show you which devices are most vulnerable to attack. This lets you prioritize your risk mitigation plans and helps you comply with regulatory frameworks that require you to identify and prioritize all vulnerabilities.
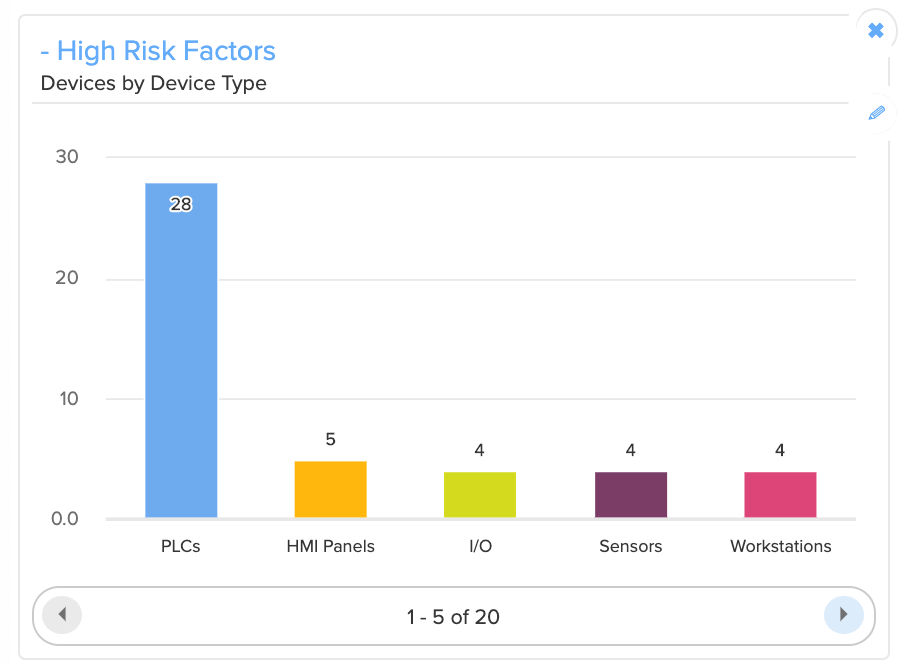
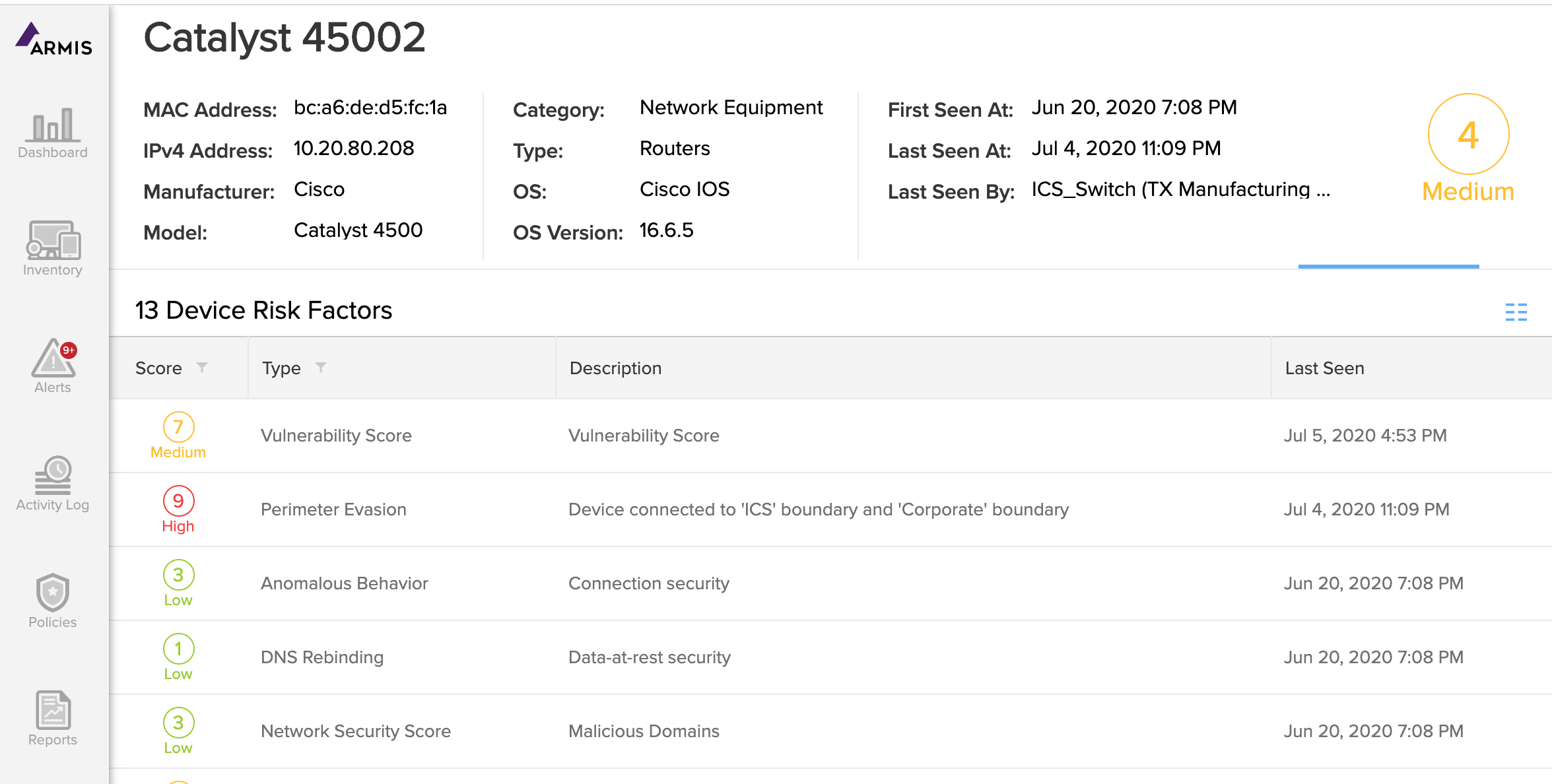
The Armis agentless device security platform automatically performs an ICS Security Risk Assessment for each device in your environment. The risk assessment includes an overall risk score for each device along with detailed information about the factors that make up each device’s risk profile, such as:
- Connectivity methods
- Connectivity behavior
- Use of cloud resources
- Data at rest security
- Software versions
- Authentication security
- Manufacturer reputation
- The scores produced by the Armis ICS
Security Risk Assessment help you take proactive steps to reduce your attack surface, and they also help you comply with regulatory frameworks that require you to identify and prioritize all vulnerabilities.
Detect Specific OT Communication Risks
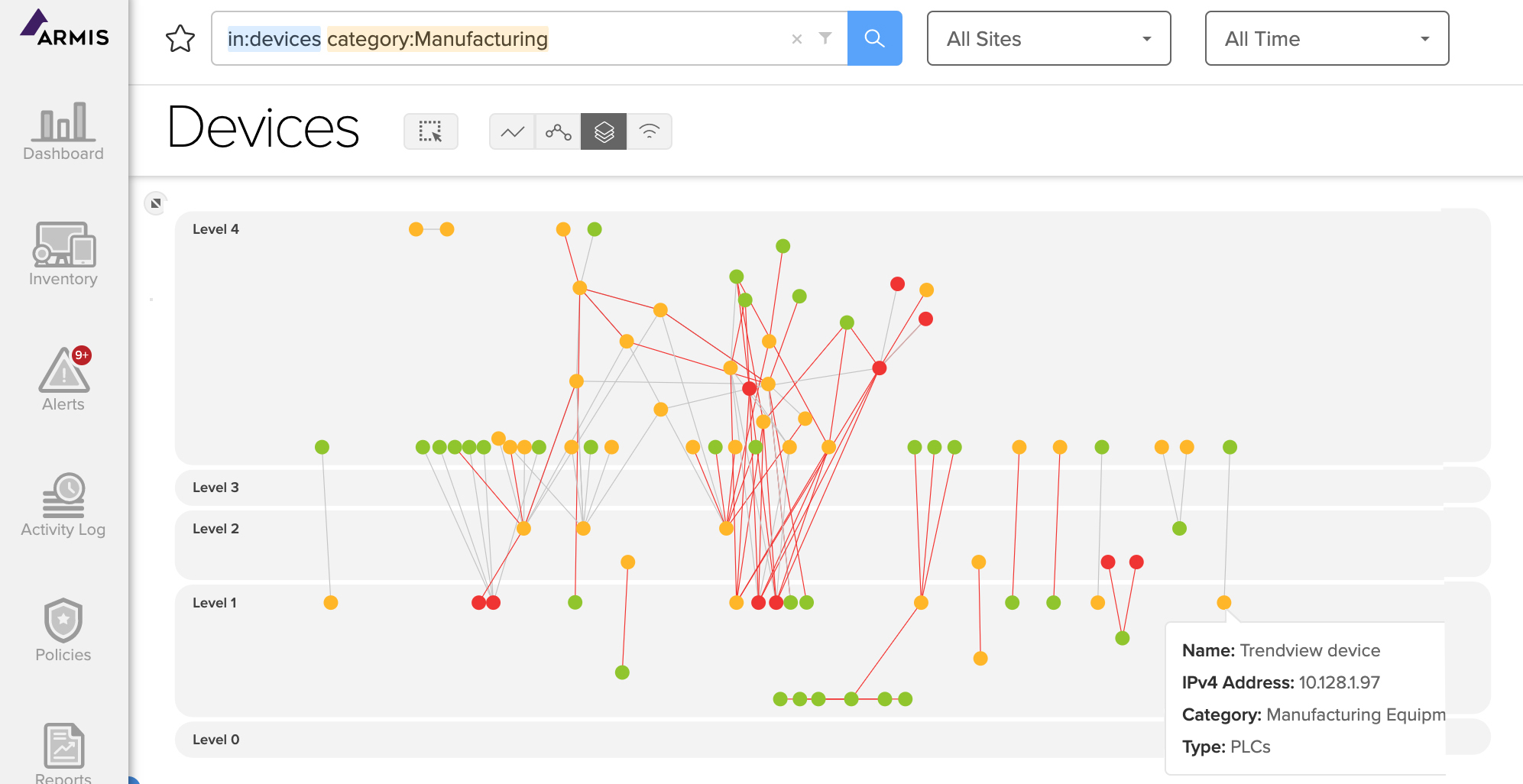
Armis can also help you assess the security risks in your OT communication architecture. Most OT environments are modeled after the Purdue reference architecture which shields vulnerable OT devices from attack by limiting their connections. But in practice, the Purdue model is often implemented imperfectly. There are often many loopholes and segmentation violations.
Armis provides visibility to devices on levels 0 through 5 of the Purdue reference architecture, including the connections between all devices. This visibility lets you identify risky connections and violations in your environment.
Specific ICS Risk Insights
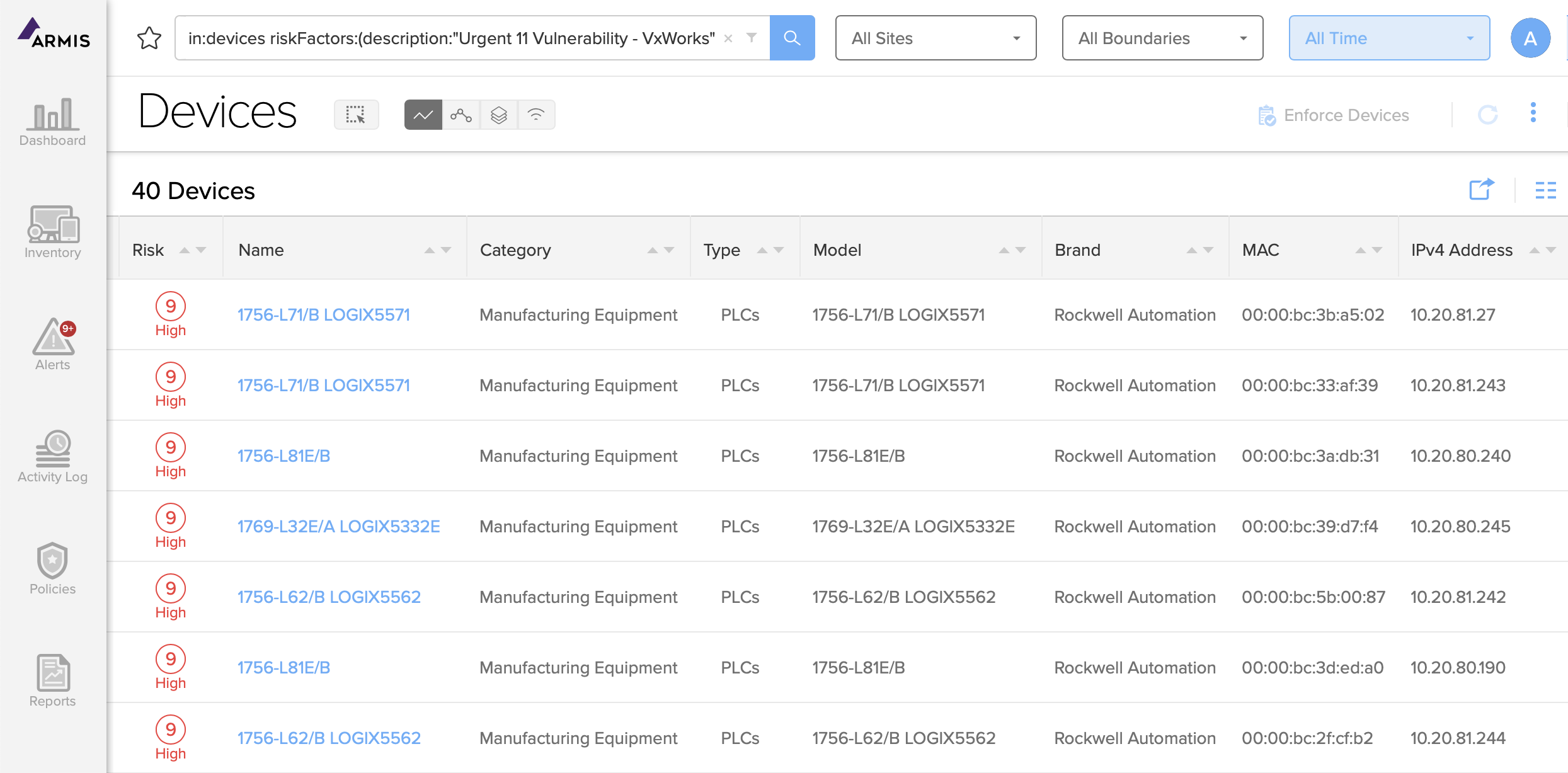
Avoid Costly Operational Downtime
Sensitive industrial control systems (ICS) are vulnerable to attacks that can halt your entire operation. And every minute a manufacturing line isn't online can have catastrophic effects on an organization's bottom line. The Armis OT cyber security platform keeps you running by:
- Identifying vulnerable OT devices in your environment
- Monitoring device behavior to detect compromises or policy violations
- Stopping attacks from moving laterally from device to device
- Taking action to quarantine suspicious or malicious devices